On Monday, Google announced that it is simplifying the process of enabling two-factor authentication (2FA) for users with personal and work accounts.
Also called two-step verification (2SV), it aims to add an extra layer of security to users’ accounts to prevent siphoning attacks if passwords are stolen.
The new change involves adding a second-step method, such as an authentication app or a hardware security key, before turning on 2FA, thereby eliminating the need to use the less secure SMS-based authentication.
“This is particularly useful for organizations using Google Authenticator (or other equivalent time-based one-time password (TOTP) applications),” the company said. “Previously, users had to activate 2SV with a phone number before they could add an Authenticator.”
Users with hardware security keys have two options to add them to their accounts, including registering FIDO1 credentials on the hardware key or assigning an access key (ie FIDO2 credentials) to one.

Google notes that Workspace accounts may still be required to enter their passwords along with their passcode if the admin policy to “Allow users to skip passwords when signing in using passwords” is turned off.
In another notable update, users who choose to turn off 2FA in their account settings will no longer automatically remove recorded second steps.
“When an admin turns off 2SV for a user from the Admin console or through the Admin SDK, the second factors will be removed as before to ensure that the user’s off-board workflows remain unaffected,” Google said.
The development comes after the search giant said more than 400 million Google Accounts started using passwords in the past year for password-less authentication.
Modern authentication methods and standards such as FIDO2 are designed to resist phishing and session hijacking attacks by using cryptographic keys generated by and connected to smartphones and computers to authenticate users, as opposed to a password that can easily be stolen through credential harvesting or thief malware.
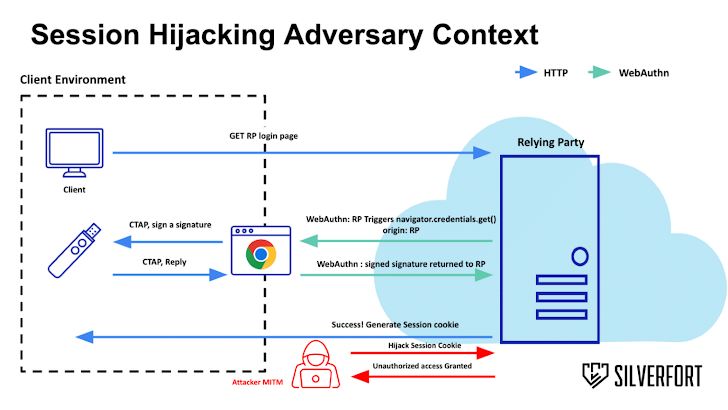
However, new research from Silverfort has found that a threat can bypass FIDO2 by staging an adversary-in-the-middle (AitM) attack that can hijack user sessions in applications that use single sign-on (SSO) solutions such as Microsoft Entra ID, PingFederate, and Yubico.
“A successful MitM attack exposes the entire request and response content of the authentication process,” said security researcher Dor Segal.
“When finished, an adversary can acquire the generated state cookie and hijack the session from the victim. Simply put, there is no validation from the app after authentication is complete.”

The attack is possible due to the fact that most applications do not protect the session tokens created after successful authentication, thus allowing a bad actor to gain unauthorized access.
Moreover, there is no verification of the device that requested the session, meaning that any device can use the cookie until it expires. This makes it possible to bypass the authentication step by acquiring the cookie through an AitM attack.
To ensure that the authenticated session is used solely by the client, it is recommended to adopt a technique known as token binding, which allows applications and services to cryptographically bind their security tokens to the transport layer security protocol layer ( TLS).
Although token binding is limited to Microsoft Edge, Google last month announced a new feature in Chrome called Device Bound Session Credentials (DBSC) to protect users against session cookie theft and hijacking attacks.



