Chinese-speaking users are the target of an unprecedented cluster of codename threat activity Empty Arachne which uses malicious Windows Installer (MSI) files for virtual private networks (VPNs) to deliver a command and control (C&C) framework called Winos 4.0.
“The campaign also promotes compromised MSI files embedded with nudifiers and software to generate deep fake pornography, as well as AI voice and facial technologies,” Trend Micro researchers Peter Girnus, Aliakbar Zahrawi and Ahmed Mohamed Ibrahim said in a technical report published today .
“The campaign uses [Search Engine Optimization] poisoning tactics and social media and messaging platforms to spread malware.”
The security vendor, which discovered the new threat group in early April 2024, said the attacks included advertising popular software such as Google Chrome, LetsVPN, QuickVPN and Telegram’s Simplified Chinese Language Pack for Winos distribution. Alternative attack chains take advantage of backdoor installers distributed in Chinese-language themed Telegram channels.

Links that appeared through black hat SEO tactics point to a special infrastructure created by the adversary to deliver installers in the form of ZIP archives. For attacks targeting Telegram channels, MSI installers and ZIP archives are hosted directly on the messaging platform.
The use of a malicious Chinese language pack is interesting not least because it presents a huge attack surface. Other types of software claim to offer the ability to generate deeply fake pornographic videos without consent for use in sexual extortion scams, AI technologies that can be used for virtual kidnapping, and voice and face-altering tools.
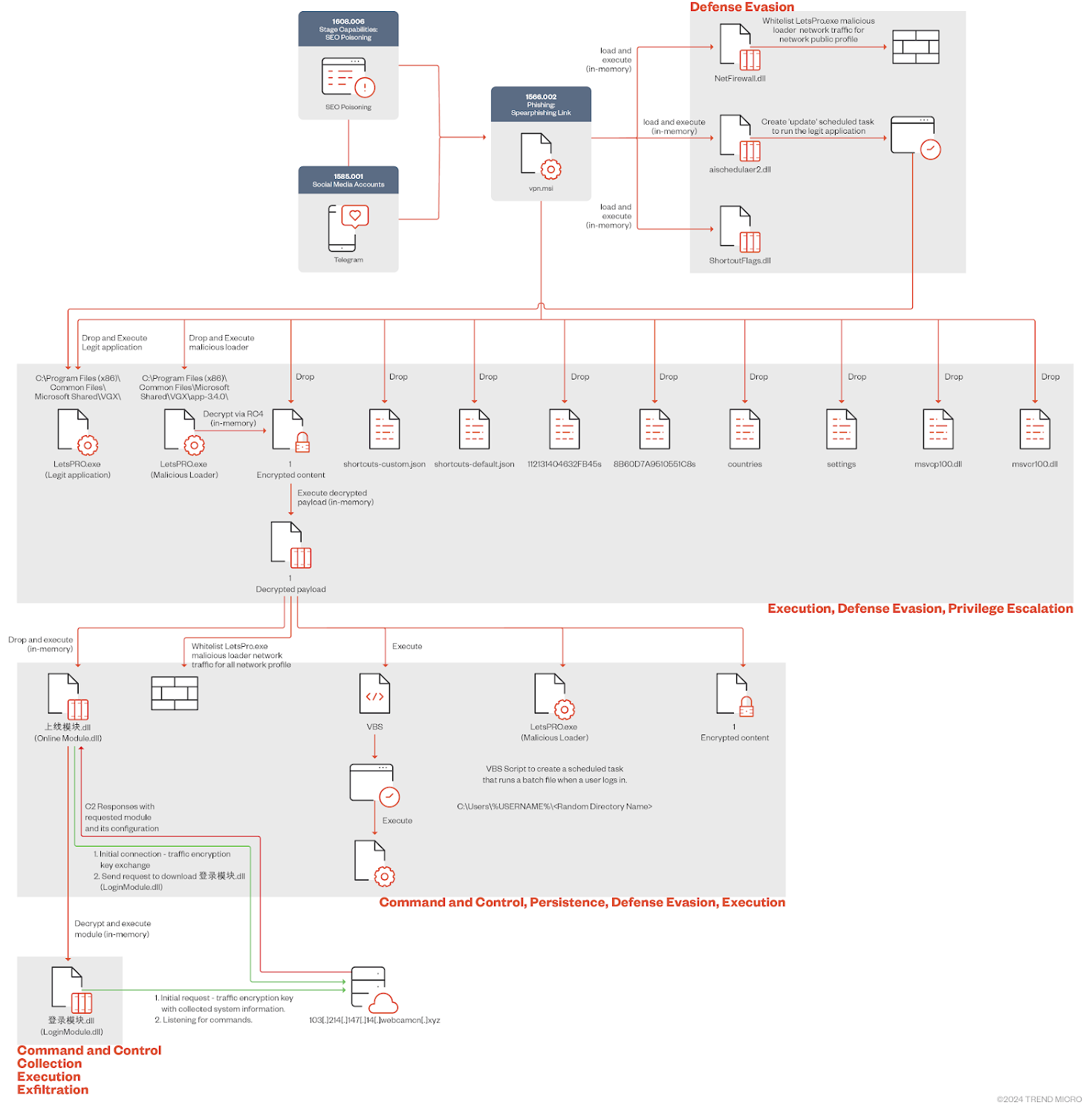
Installers are designed to modify firewall rules to allow inbound and outbound traffic associated with the malware when connected to public networks.
It also drops a loader that decrypts and executes a second-stage payload in memory, which then runs a Visual Basic Script (VBS) to set up host persistence and trigger the execution of an unknown batch script and deliver the Winos 4.0 C&C framework through a stager that establishes C&C communications with a remote server.
An implant written in C++, Winos 4.0 is equipped with file management, Distributed Denial of Service (DDoS) using TCP/UDP/ ICMP/HTTP, disk search, webcam control, screenshot capture, microphone recording , logging keystrokes and remote shell access .
Underscoring the complexity of the backdoor is a plugin-based system that implements the aforementioned functions through a set of 23 special components compiled for both 32- and 64-bit variants. It can be further extended by external plugins integrated by the threat actors themselves depending on their needs.

The core component of WinOS also includes methods to detect the presence of security software distributed in China, in addition to acting as a master orchestrator responsible for loading plugins, clearing system logs, and downloading and executing additional payloads from URL provided.
“Internet connectivity in the People’s Republic of China is subject to strict regulation through a combination of legislative measures and technological controls, collectively known as the Great Firewall of China,” the researchers noted.
“Due to strict government controls, VPN services and public interest in this technology have greatly increased. This, in turn, has fueled threat actors’ interest in exploiting the increased public interest in software that can evade the Great Firewall and online censorship.”