Cybersecurity researchers have discovered an updated version of a banking Trojan for Android called Medusa which was used to target users in Canada, France, Italy, Spain, Turkey, the United Kingdom, and the United States
The new fraud campaigns, observed in May 2024 and active since July 2023, manifest through five different botnets run by different affiliates, cybersecurity firm Cleafy said in an analysis published last week.
The new Medusa samples include “a light set of permissions and new features, such as the ability to display a full-screen overlay and remotely uninstall apps,” security researchers Simone Mattia and Federico Valentini said.
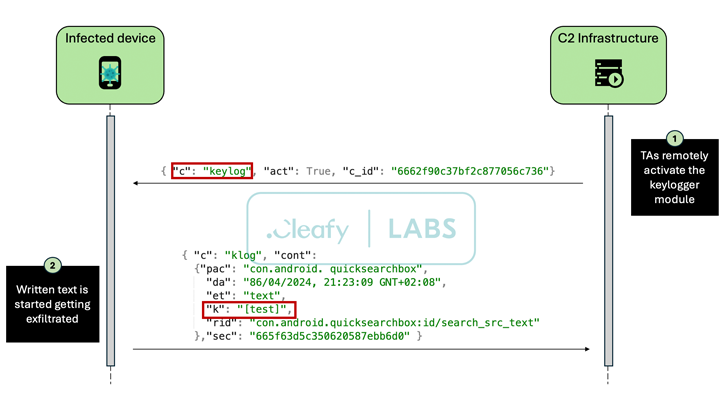
Medusa, also known as TangleBot, is a sophisticated Android malware first discovered in July 2020 targeting financial entities in Turkey. It comes with capabilities to read SMS messages, log keystrokes, capture screenshots, record calls, share the device’s screen in real-time, and perform unauthorized money transfers using bank identity theft overlay attacks data.

In February 2022, ThreatFabric uncovered Medusa campaigns using similar delivery mechanisms to those of FluBot (aka Cabassous), disguising the malware as seemingly harmless package delivery and utility applications. The threats behind the Trojan are suspected to be from Turkey.
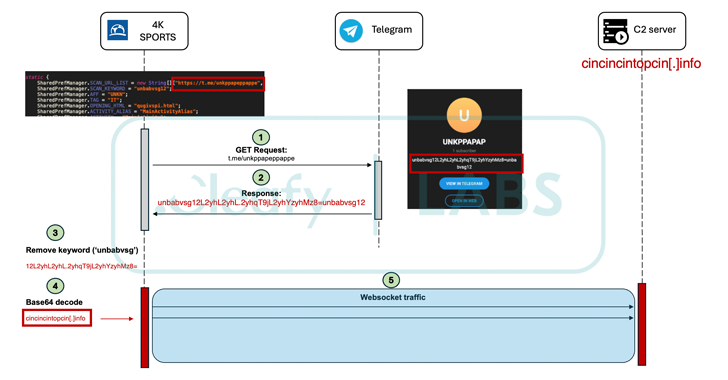
Cleafy’s latest analysis reveals not only malware enhancements, but also the use of drippers to distribute Medusa under the guise of fake updates. In addition, legitimate services such as Telegram and X are used as dead-end converters to extract the command and control (C2) server used to exfiltrate data.
A notable change is the reduction in the number of permits sought in an apparent effort to reduce the chances of detection. However, it still requires the Android Accessibility Services API, which allows it to covertly enable other permissions as required and avoid raising suspicion among users.
Another modification is the ability to set a black screen overlay on the victim’s device to give the impression that the device is locked or turned off and used as a cover for malicious activities.
Medusa botnet clusters typically rely on tried and tested approaches such as phishing to spread malware. However, more recent waves have been seen spreading it via drip apps downloaded from untrusted sources, highlighting the ongoing efforts by threat actors to evolve their tactics.
“Minimizing the required permissions avoids detection and appears more favorable by improving its ability to operate undetected for extended periods,” the researchers said. “Geographically, the malware is expanding into new regions, such as Italy and France, indicating a deliberate effort to diversify its victim pool and expand its attack surface.”

The development comes after Symantec revealed that bogus Chrome browser updates for Android were being used as bait to remove the Cerberus banking trojan. Similar campaigns distributing fake Telegram apps through fake websites (“telegrams[.]icu”) have also been observed to distribute another Android malware called SpyMax.
Once installed, the app prompts the user to enable accessibility services, allowing it to collect keystrokes, exact locations, and even the speed at which the device is moved. The collected information is then compressed and exported to an encrypted C2 server.
“SpyMax is a Remote Administration Tool (RAT) that has the ability to collect personal/confidential information from an infected device without user consent and send it to a remote threat actor,” K7 Security Labs said. “This allows threat actors to control victims’ devices, impacting the privacy and integrity of the victim’s privacy and data.”