Getty Images
Threat actors had been carrying out zero-day attacks targeting Windows users with malware for more than a year before Microsoft patched the vulnerability that made them possible, researchers said Tuesday.
The vulnerability, present in both Windows 10 and 11, causes devices to open Internet Explorer, a legacy browser that Microsoft retired in 2022 after its outdated code base made it increasingly vulnerable to exploits. Since the move, Windows has made it difficult, if not impossible, to open the normal browser that was first introduced in the mid-1990s.
Old and new tricks
Malicious code that exploits the vulnerability dates back to at least January 2023 and circulated in May of this year, according to the researchers who discovered the vulnerability and reported it to Microsoft. The company patched the vulnerability, tracked as CVE-2024-CVE-38112, on Tuesday as part of its monthly patch release program. The vulnerability, which resided in the Windows MSHTML engine, had a severity rating of 7.0 out of 10.
Researchers at security firm Check Point said the attack code performed “new (or previously unknown) tricks to lure Windows users into remote code execution.” A link that appeared to open a PDF file added a .url extension to the end of the file, such as Books_A0UJKO.pdf.url found in one of the malicious code samples.
When viewed in Windows, the file displays an icon indicating that the file is a PDF and not a .url file. Such files are intended to open an application specified in a link.

Check Point
A link in the file made a call to msedge.exe, a file that runs Edge. However, the link includes two attributes – mhtml: and !x-usc: – an “old trick” that threat actors have used for years to get Windows to open applications like MS Word. It also includes a link to a malicious website. When clicked, the .url file masquerading as a PDF opens the site in Internet Explorer, not Edge.
“From there (the website is opened with IE), an attacker can do a lot of bad things because IE is insecure and outdated,” wrote Haifei Li, the Check Point researcher who discovered the vulnerability. “For example, if an attacker has an IE zero-day exploit – which is much easier to find than Chrome/Edge – the attacker can attack the victim to get immediate remote code execution. However, in the samples we analyzed, the threat actors did not use an IE remote code execution exploit. Instead, they used another trick in IE – which probably wasn’t publicly known until now – as far as we know, to trick the victim into getting remote code execution.”
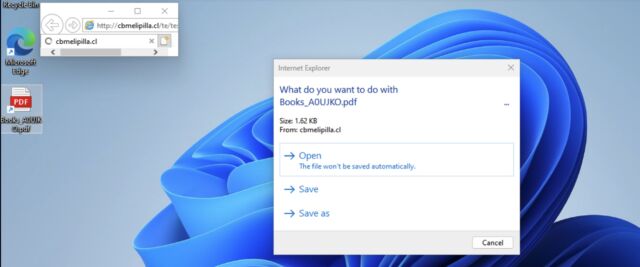
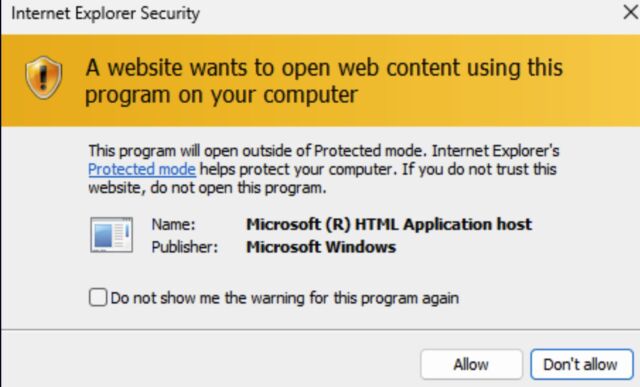
IE will then present the user with a dialog asking them if they want to open the file disguised as a PDF. If the user clicks open, Windows presents a second dialog box showing a vague message that continuing will open the contents of the Windows drive. If users click “allow,” IE will load a file ending in .hta, an extension that causes Windows to open the file in Internet Explorer and execute embedded code.
Check Point
Check Point
“To summarize the attacks from an exploit perspective: the first technique used in these campaigns is the ‘mhtml’ trick, which allows the attacker to invoke IE instead of the more secure Chrome/Edge,” Li wrote. “The second technique is a trick on IE to trick the victim into believing they are opening a PDF file when they are actually downloading and running a dangerous .hta application. The common goal of these attacks is to trick victims into believing that they are opening a PDF file, and this is possible with the help of these two tricks.
Check Point’s post includes cryptographic hashes for six malicious .url files used in the campaign. Windows users can use the hashes to verify that they have been targeted.



