The Advanced Persistent Threat Team (APT) is on call. Blank Banshee was observed using a recently disclosed security flaw in the Microsoft MHTML browser engine as a zero-day to deliver an information thief called Atlantida.
Cybersecurity firm Trend Micro, which monitored activity in mid-May 2024, said the vulnerability — tracked as CVE-2024-38112 — was exploited as part of a multi-stage attack chain using specially crafted Internet shortcut (URL) files.
“Variants of the Atlantida campaign were very active in 2024 and evolved to exploit CVE-2024-38112 as part of Void Banshee infection chains,” said security researchers Peter Girnus and Aliakbar Zahravi. “The ability of APT groups like Void Banshee to exploit disabled services such as [Internet Explorer] poses a significant threat to organizations around the world.”

The findings match previous disclosures from Check Point, which told The Hacker News about a campaign using the same flaw to spread the thief. It’s worth noting that CVE-2024-38112 was addressed by Microsoft as part of last week’s Patch Tuesday updates.
CVE-2024-38112 is described by the Windows manufacturer as a rogue vulnerability in the MSHTML (aka Trident) browser engine used in the now-discontinued Internet Explorer browser. However, the Zero Day Initiative (ZDI) claims that this is a remote code execution bug.
“What happens when a vendor says a patch should be a Defense-in-Depth update and not a full CVE?,” ZDI’s Dustin Childs pointed out. “What happens when a vendor claims the impact is tampering, but the bug leads to remote code execution?”
Attack chains include the use of phishing emails embedding links to ZIP archive files hosted on file sharing sites that contain URL files that exploit CVE-2024-38112 to redirect the victim to a compromised site hosting a malicious HTML application (HTA ).
Opening the HTA file causes a Visual Basic Script (VBS) to be executed, which in turn downloads and executes a PowerShell script responsible for extracting the .NET bootloader horse, which ultimately uses the Donut shellcode project to decrypt and execute Atlantida thief in the memory of the RegAsm.exe process.
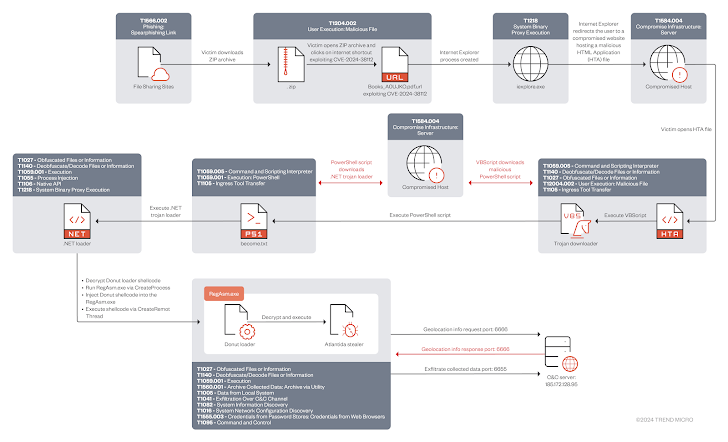
Atlantida, modeled after open-source thieves like NecroStealer and PredatorTheStealer, is designed to extract files, screenshots, geolocation and sensitive data from web browsers and other applications, including Telegram, Steam, FileZilla and various cryptocurrency wallets.
“By using specially crafted URL files that contained the MHTML protocol handler and the x-usc! directive, Void Banshee was able to access and launch HTML application (HTA) files directly through the disabled IE process,” the researchers said.
“This exploit is similar to CVE-2021-40444, another MSHTML vulnerability that has been exploited in zero-day attacks.”
Not much is known about the Void Banshee other than the fact that it has a history of targeting regions of North America, Europe and Southeast Asia for information theft and financial gain.
The development comes after Cloudflare revealed that threat actors are quickly incorporating proof-of-concept (PoC) exploits into their arsenal, sometimes even 22 minutes after their public release, as seen in the case of CVE-2024-27198.
“The speed at which exposed CVEs are exploited is often faster than the speed at which people can create WAF rules or create and deploy patches to mitigate attacks,” the web infrastructure company said.
It also follows the discovery of a new campaign that uses Facebook ads promoting fake Windows themes to spread another thief known as SYS01stealer, which aims to hijack business Facebook accounts and spread the malware.
“As an information thief, SYS01 focuses on exfiltrating browser data such as credentials, history and cookies,” Trustwave said. “Much of its payload is focused on obtaining access tokens for Facebook accounts, specifically those with Facebook business accounts, which can help threat actors distribute malware.”



