Stay informed with free updates
Just sign up at Technology sector myFT Digest – delivered straight to your inbox.
The writer is a professor at Tufts and author of “Cyber Insurance Policy’
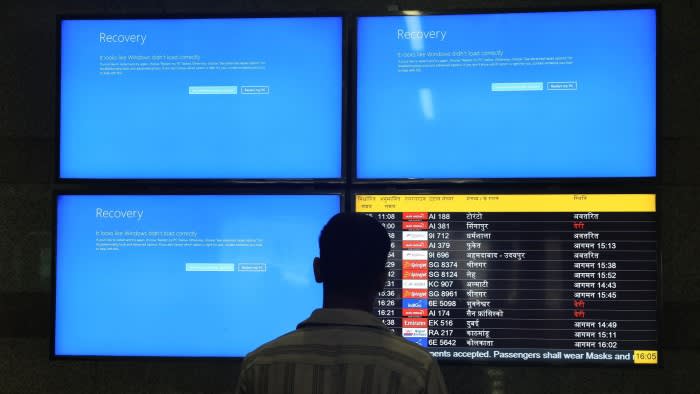
Who is to blame for the CrowdStrike software outage that took down millions of computers in every industry sector around the world last week? As is often the case with cybersecurity incidents, there are many accusations. CrowdStrike failed to properly verify the channel file it sent to its customers, crashing their Windows computers, and it also appears that they distributed this file to everyone at once instead of starting with a small number of customers to identify any issues before release the update widely.
Meanwhile, Microsoft allowed CrowdStrike and other third-party developers to gain kernel-level access to its Windows operating system. The operating system kernel controls the entire computer. Without this level of access, CrowdStrike’s update likely wouldn’t have had the same impact. It would certainly be easier to fix without manually rebooting all affected systems.
Giving software companies this kind of access to an operating system is dangerous — it means you can quickly lose control of your computer if one of the software vendors you rely on makes a mistake or is compromised. This is why Apple began informing third-party developers in 2020 that it would no longer provide them with kernel-level access to the MacOS operating system (and also, quite possibly, why the CrowdStrike issue did not affect Apple devices).
But it’s not all Microsoft’s fault. A 2009 agreement between the company and the European Commission requires it to give outside developers the same access to Windows that its own security software has. The idea was to enable other software companies to compete with Microsoft by ensuring that many of its products and services were compatible with external software and tools. This is a worthy goal, and many provisions in the agreement are perfectly reasonable, such as requiring Outlook to support common calendar events and scheduling formats.
But the 2009 agreement is deeply flawed by requiring Microsoft to make any APIs or programming features that its own security software products use available to third-party security software vendors. It’s the provision that requires Microsoft to provide kernel-level access to companies like CrowdStrike. Until that’s changed, it’s unclear whether Microsoft can take the main lesson from that failure and start phasing out access like Apple did four years ago.
In addition to changing its agreement with Microsoft, the commission – like other regulators – must consider the risks of sacrificing security in the name of competition. Tech companies have long warned that opening up too much of their ecosystem to outside developers could come at the cost of security. These concerns are sometimes dismissed as an excuse for anti-competitive behavior, but there are some legitimate trade-offs between security and competition.
The commission last month said that Apple, to comply with the EU’s Digital Markets Act, must make it easier to access and download software provided outside its official App Store. This will open up more competition for apps, but could mean users download insecure software that hasn’t been vetted by Apple.
Encouraging competition like this absolutely requires operating systems to be locked down as much as possible because we could end up downloading software from very unknown and untrustworthy developers. That’s why Apple introduced new security measures to its mobile operating system in January to limit potential damage from unverified code downloaded to iPhones. That’s why regulators need to carefully consider the level of access they insist technology companies provide to competitors and third-party developers.
We may be willing to sacrifice some security for the sake of more competition, but we should never, under any circumstances, sacrifice our computer cores.